Because of the way it is constructed, the virtual currency bitcoin offers a novel realization of a central bank-free financial instrument, as well as an alternative approach to classical distributed computing problems, and to numerous other applications, such as smart electronic contracts.
At the core of bitcoin is the blockchain, which is essentially a long line of chained blocks containing data (namely, fund-transferring transactions) that is the enabling technology underneath the application. Those who attempt to build blockchains are called miners.
 Dr. Juan Garay, a professor in the Department of Computer Science and Engineering at Texas A&M University, is focused on understanding the fundamental properties of the blockchain data structure and protocol.
Dr. Juan Garay, a professor in the Department of Computer Science and Engineering at Texas A&M University, is focused on understanding the fundamental properties of the blockchain data structure and protocol.
“It is called a protocol because it is a collection of programs, one for each participant,” Garay said. “There are multiple participants that perform so-called 'proofs of work' and exchange messages. My work was the first to formally define this, analyze it and prove the basic properties of the underlying data structure.”
Garay’s paper titled, “The Bitcoin Backbone Protocol: Analysis and Applications” was among Coindesk’s top 10 2015 cryptocurrency research papers.
The blockchain implements a distributed ledger, which keeps records of the transactions between the bitcoin users. New transactions are added to the ledger when one of the miners generates a proof of work, generating a new block, which is then added to the blockchain.
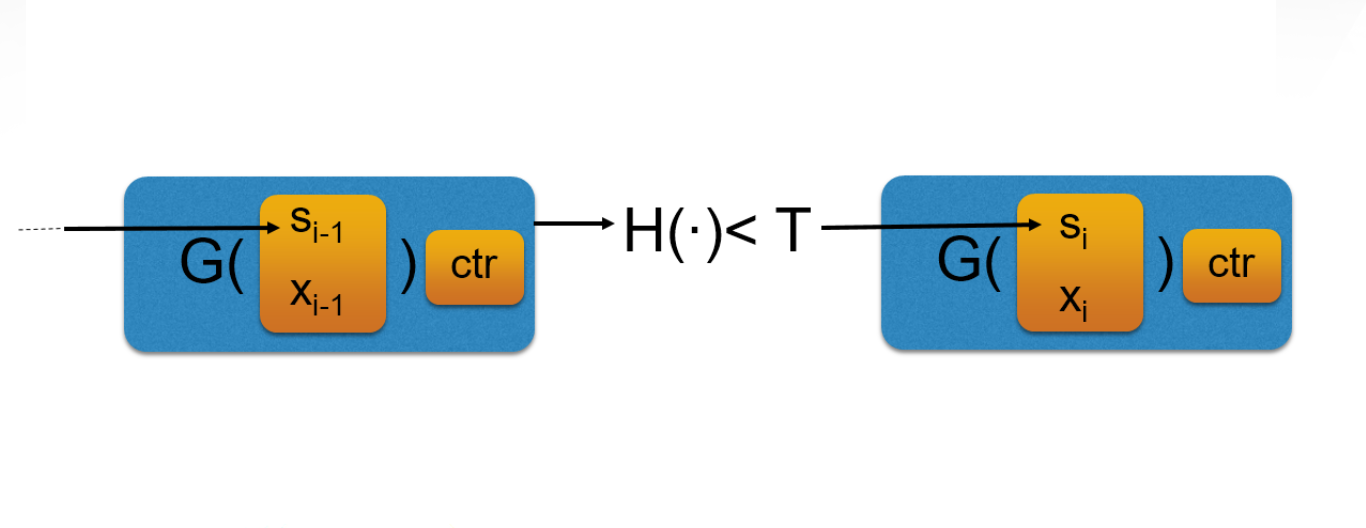
Proofs of work are generated by miners solving an algorithmic problem - these days using specialized hardware, which expends energy to compute. In bitcoin, a solution to a proof of work is found when the output of a cryptographic hash function - a random function that maps arbitrary inputs to a small domain - applied to the current state of the blockchain and new transactions is smaller than a predetermined value.
“Proofs of work, a cryptographic primitive originally designed to combat spam email, and which also goes by the name of 'cryptographic puzzles', allows a party (the prover) to convince another party (the verifier), that she/he has invested a considerable amount of effort in solving a computational problem,” Garay said. “My work aims to rigorously formulate such properties, and then show how applications can be formally derived from them. This entails the specification and contrast of computational models on which blockchain protocols are run, together with the required trusted setup and computational assumptions and the cryptographic tools that enable their operation.”
Garay’s broader research focus is cryptographic protocols and schemes, which play a fundamental role in enabling new functionalities and privacy-preserving ways of interaction in today’s digital world. Garay first began studying the subject of blockchain protocols over three years ago and has since played a vital role in the continuous research on the subject.
Header Image: An abstract representation of blocks in a blockchain. G and H are cryptographic hash functions, and the xi's represent transactions. The second block is linked to the first block by a solution of the cryptographic puzzle that includes information from the first block.